Latest
TECH NEWS
How To
Easily Change the RDP Port on Windows 10 for Secure Remote Access
Easily Change the RDP Port on Windows 10 for Secure Remote Access The Remote Desktop…
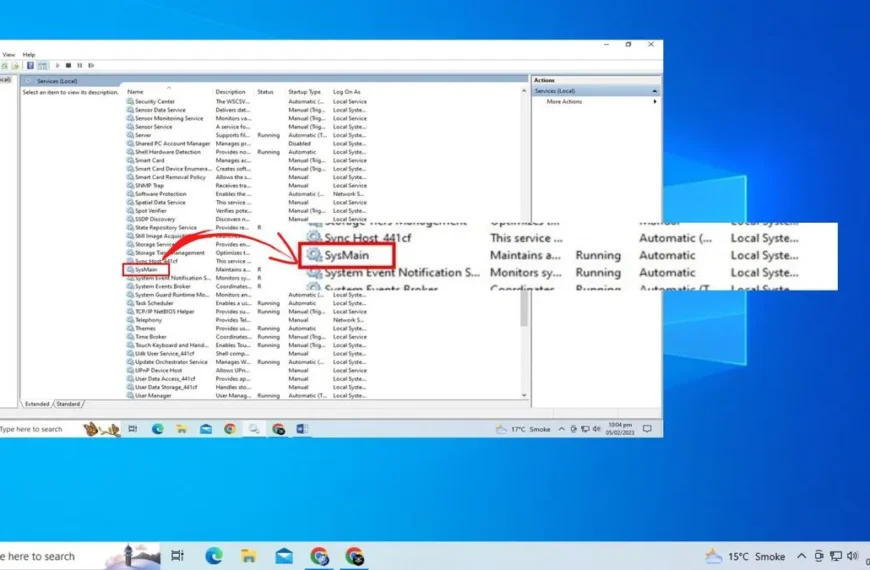
Effortlessly Disable Superfetch on Windows 10 with this Guide
Disable Superfetch on Windows 10 Superfetch is a feature in Windows 10 that helps improve…
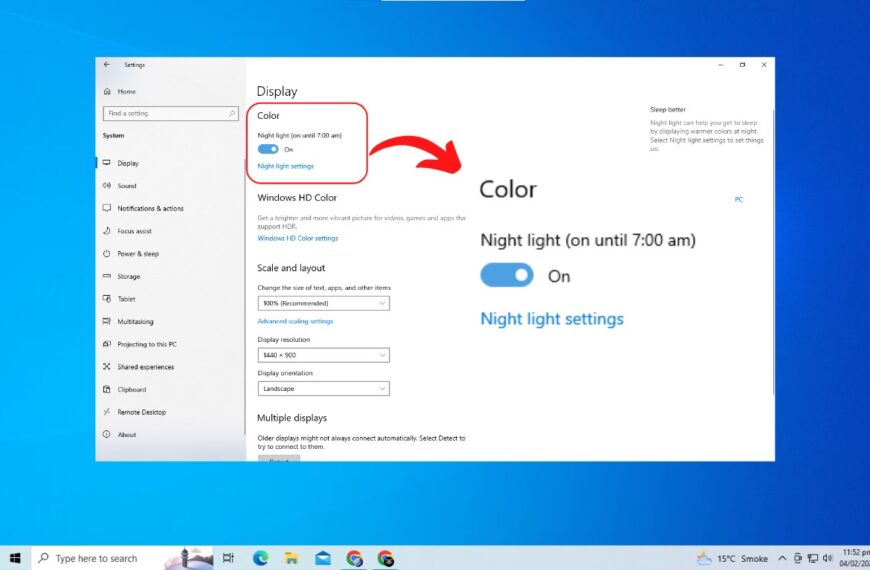
Maximizing Comfort and Minimizing Blue Light: How to Enable Night Light in Windows 10
Why people use Night light Mode in Windows People use Night Light mode in Windows…
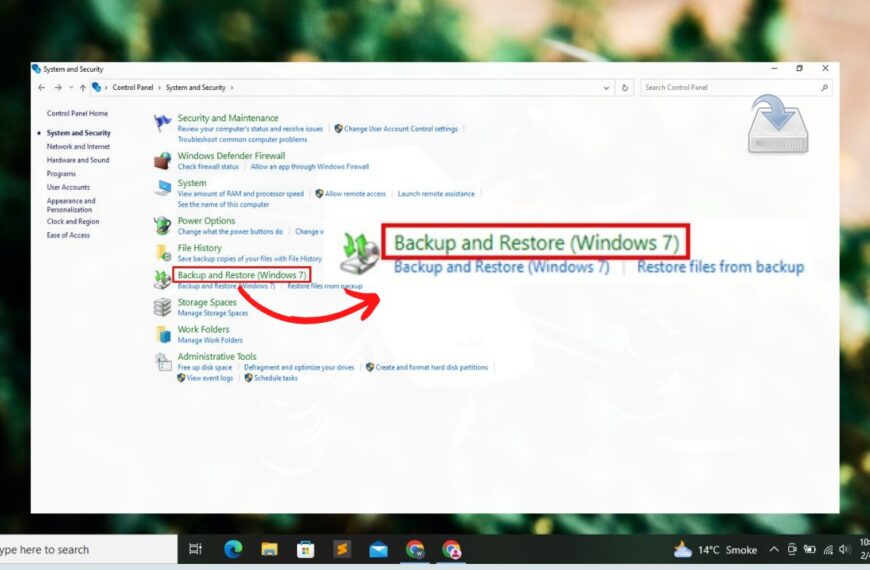
How to Take Backup of Windows 10
How to Take Backup of Windows 10 Windows 10 provides several options to backup the…
Maximizing Media Enjoyment: The Screen-Off Experience
Maximizing Media Enjoyment: The Screen-Off Experience Are you tired of holding your phone or tablet…
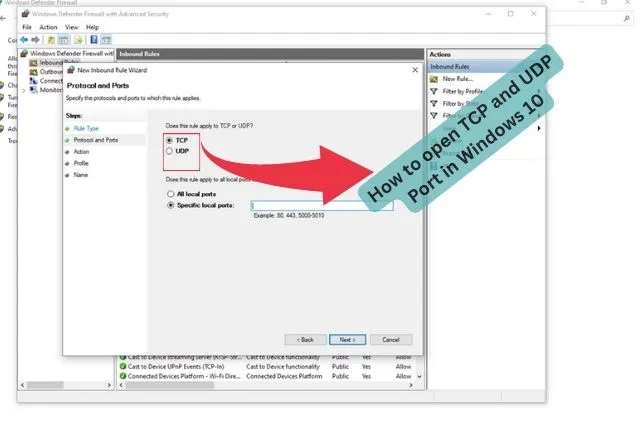
How to open TCP and upd port in Windows 10
How to open TCP and upd port in Windows 10 How to open TCP and…
Apple
Stay Connected and Stylish: A Guide to Apple Watch Fashion
Stay Connected and Stylish: A Guide to Apple Watch FashionThe Perfect FitMatch Made in HeavenDress…
The Apple Touch: How Intuitive Design Enhances User Experience
The Apple Touch: How Intuitive Design Enhances User ExperienceThe Power of SimplicitySeamless IntegrationIntuitive Gestures and…
Gadget Wonderland: Apple’s Spectacular Offerings
Gadget Wonderland: Apple’s Spectacular OfferingsThe iPhone PhenomenonUnleashing the Power of iPadsAirPodsBeyond the EssentialsThe Magic of…
The best iPhone accessories you need in 2023
The best iPhone accessories you need in 2023Wireless Charging PadAirPods ProPopSocketSmart Battery CaseCamera Lens KitApple…
Uncover the Best-Kept Secrets of Your iPhone: 10 Hidden Features You Never Knew Existed
Uncover the Best-Kept Secrets of Your iPhone: 10 Hidden Features You Never Knew ExistedBack TapMedical…
The Apple Watch: An In-Depth Analysis of Apple’s Wearable Technology
The Apple Watch: An In-Depth Analysis of Apple’s Wearable TechnologyDesign:Features:Impact on Wearable Technology:Conclusion: The Apple…
Windows
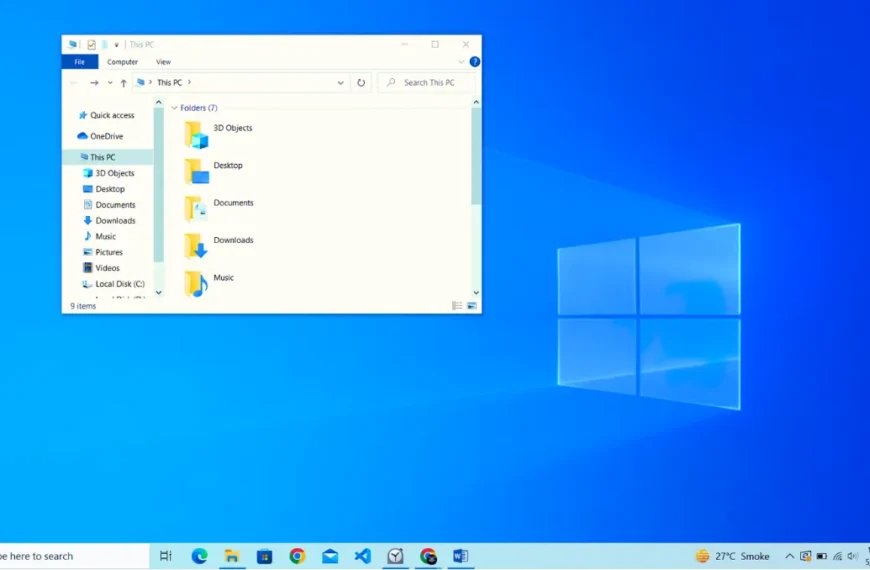
How to Manage Files and Folders in Windows: Organize and Access with Ease
How to Manage Files and Folders in Windows: Organize and Access with EaseCreate a Folder…
Windows Gaming Devices: Unleashing the Power of PC Gaming
Windows Gaming Devices: Unleashing the Power of PC GamingAdvantages on windows gaming devicesExtensive Hardware OptionsCompatibility…
Common file and folder permission errors and how to troubleshoot them
Common file and folder permission errors and how to troubleshoot themCommon File and Folder Permission…
Windows Registry: Best Way Understanding and Optimizing Your PC’s System Settings
Windows Registry: Best Way Understanding and Optimizing Your PC’s System SettingsUnderstanding the Windows RegistryOptimizing Your…
Managing Driver Conflicts:Best Tools and Techniques for Smooth System Operation
Managing Driver Conflicts:Best Tools and Techniques for Smooth System Operation Managing Driver Conflicts:Best Tools and…
Windows Networking: Optimizing Your PC’s Connection for Faster and More Reliable Internet
Windows Networking: Optimizing Your PC’s Connection for Faster and More Reliable InternetUpdate your drivers and…
Software u0026amp; Apps
App Analytics: Unlocking Insights for Growth
App Analytics: Unlocking Insights for GrowthWhat are App Analytics?Understanding User…
Software Integration: Streamlining Processes for Seamless Operations
Software Integration: Streamlining Processes for Seamless OperationsThe Significance of Software…
App Mania: Exploring the World of Mobile Applications
App Mania: Exploring the World of Mobile ApplicationsThe Significance of…
App Gamification: Adding Fun and Engagement to Applications
App Gamification: Adding Fun and Engagement to ApplicationsWhat is App…
App Discovery: Finding Hidden Gems in the Digital Marketplace
App Discovery: Finding Hidden Gems in the Digital MarketplaceDiversify Your…
App Development: From Concept to App Store
App Development: From Concept to App StoreConceptualization and ResearchWireframing and…
CYBER SECURITY
Cybersecurity Chronicles: Protecting Your Digital World
Table of Contents[Open][Close]The Evolving Cyber Threat LandscapeMalware’s Sneaky TacticsPhishing ExpeditionsThe Digital Defense ArsenalAntivirus SolutionsFirewalls and…
Building a Secure Culture: Effective Strategies for Security Awareness and Training
Table of Contents[Open][Close]The Human Element in CybersecurityTailoring Your TrainingEngaging and Educating ContinuouslySimulating Real-World ScenariosPromoting a…
The Role of Next-Generation Firewalls in Modern Security Postures
Table of Contents[Open][Close]Next-Generation Firewalls Deep Packet Inspection (DPI)Application Awareness and ControlIntrusion Prevention Systems (IPS)User Identity…
Securing Your Web Applications: A Guide to IIS Security Best Practices
Table of Contents[Open][Close]A Guide to IIS Security Keep IIS and Your OS UpdatedImplement Strong AuthenticationUse…
The Future of Digital Security Systems: Emerging Trends to Watch
Digital Security SystemsAI-Powered Threat DetectionZero Trust ArchitectureIoT SecurityQuantum-Safe EncryptionCloud-Native SecurityBiometric AuthenticationPrivacy-Enhancing TechnologiesConclusion Digital Security Systems…
The Evolution of Aura Digital Security Solutions
Aura Digital SecurityThe Founding VisionThe Early Years: Innovation and GrowthEmbracing Artificial IntelligenceThe Cloud RevolutionA Comprehensive…