Latest
TECH NEWS
How To
How to Avoid Desktopanalyticscenter dot site Pop-Ups? explain step by step
How to Avoid Desktopanalyticscenter dot site Pop-Ups DesktopAnalyticsCenter.site is a website that displays pop-up advertisements.…
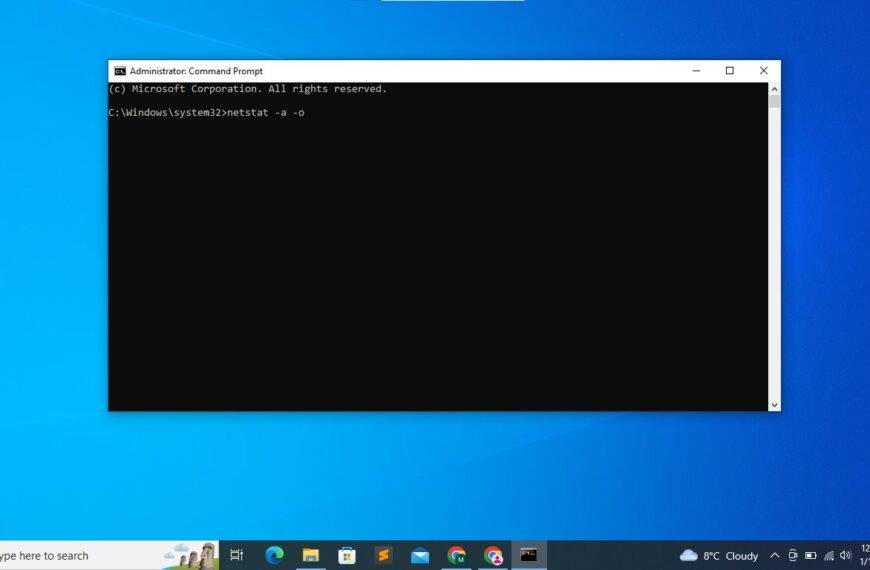
How to open TCP and upd port in Windows 10 using command Prompt
Introduction In this article, we will show you how to open TCP and UDP ports…
How to Type Faster: 5 Tips to Increase Your WPM
How to Type Faster: 5 Tips to Increase Your WPM Are you looking to increase…
how to install termux: how to use termux app
Termux is a powerful terminal emulator for Android that allows users to run various types…
Apple
Apple Support: Get Expert Assistance for Your Apple Devices and Services
Apple Support: Get Expert Assistance for Your Apple Devices and Services If you are an…
How Apple Watch is the Only Wearable Device You’ll Ever Need
How Apple Watch is the Only Wearable Device You’ll Ever Need The Apple Watch is…
Unleashing Your Inner Photographer: A Guide to Apple’s Camera Features
Unleashing Your Inner Photographer: A Guide to Apple’s Camera Features In today’s world, smartphone cameras…
The Power of Apple’s A-Series Chips: What Makes Them So Fast and Efficient
The Power of Apple’s A-Series Chips: What Makes Them So Fast and Efficient Apple’s A-Series…
Apple and Android: A Comparison of Two Popular Smartphone Operating Systems
Apple and Android: A Comparison of Two Popular Smartphone Operating Systems Smartphones have essentially become…
The Role of Apple in Shaping the Mobile Computing Landscape
Mobile computing has become an integral part of our daily lives, with smartphones and other…
Windows
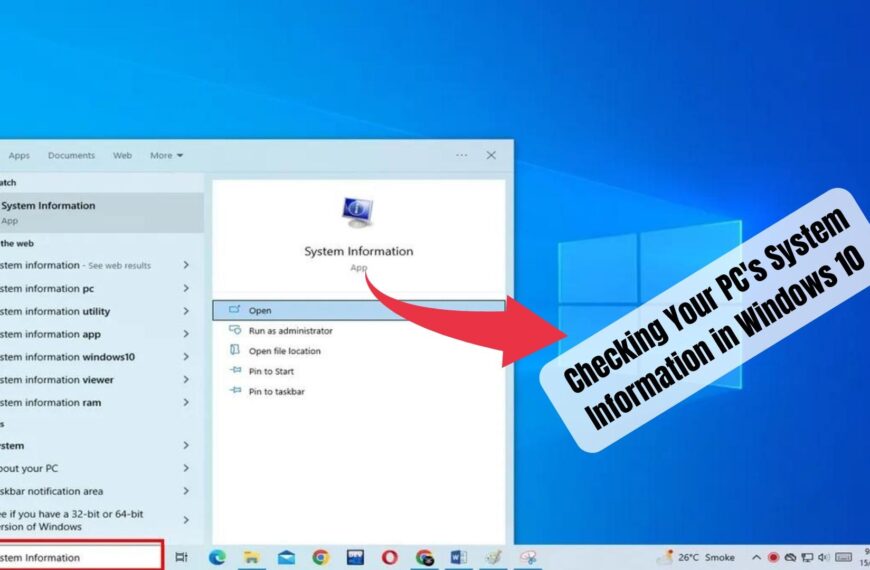
How to Check Your PC’s System Information in Windows 10
How to Check Your PC’s System Information in Windows 10 Introduction: Knowing your computer’s system…
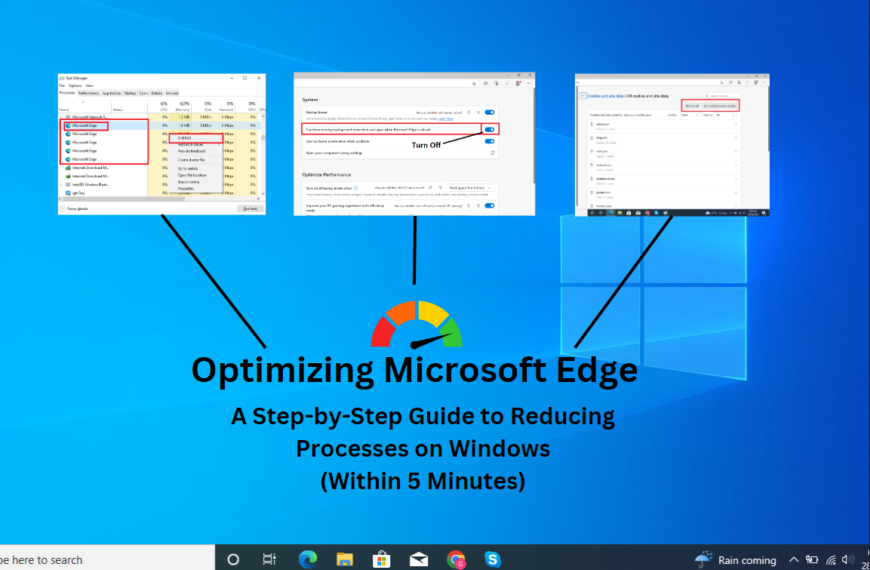
Optimizing Microsoft Edge: A Step-by-Step Guide to Reducing Processes on Windows
A Step-by-Step Guide to Reducing Processes on Windows Microsoft Edge is the default web browser…
5 Useful Windows Features You Might Have Overlooked in Windows 10
5 Useful Windows Features Windows is a powerful and feature-rich operating system, but many of…
Say Goodbye to Unnecessary Files: A Guide to Disk Cleanup in Windows 10
A Guide to Disk Cleanup in Windows 10 Keeping your hard drive organized and clutter-free…
Easily Change the RDP Port on Windows 10 for Secure Remote Access
Easily Change the RDP Port on Windows 10 for Secure Remote Access The Remote Desktop…
Get Quick Access to Your Apps with the Quick Launch Toolbar in Windows 10
The Quick Launch toolbar in Windows 10 is a powerful tool that allows you to…
Software u0026amp; Apps
Get Your Game On: The Best Mobile Games to Play on-the-go
Get Your Game On: The Best Mobile Games to Play…
Maximizing Media Enjoyment: The Screen-Off Experience
Maximizing Media Enjoyment: The Screen-Off Experience Are you tired of…
How to Open Epub file on your android phone: A step-by-step Guide
E-pub files have become the most popular format for eBooks.…
The Ultimate Guide to Using Windows on Your Mobile Device
The Ultimate Guide to Using Windows on Your Mobile Device…
Maximizing Productivity with Split Screen on the Redmi Note 11 A User’s Guide
Welcome to “Maximizing Productivity with Split Screen on the Redmi…
The Future of Inventory Management: How Software is Changing the Game
The Future of Inventory Management Inventory management is the process…
CYBER SECURITY
Protecting Intellectual Property with Digital Security Measures
Digital Security Measures In the realm of innovation and creativity, intellectual property (IP) stands as…
Navigating the Complexities of Digital Security Management
Digital Security Management In today’s hyper-connected world, where digital technologies permeate every aspect of our…
Key Features and Benefits of Digital Security Controls Products
Digital Security Controls Products In an era where digital threats lurk around every corner, the…
Implementing a Proactive Approach to Digital Security
Digital Security In the rapidly evolving digital landscape, cybersecurity threats have become more sophisticated and…
How American Digital Security is Tackling Cyber Threats
American Digital Security In an era defined by digital interconnectedness, the ever-present threat of cyberattacks…
Exploring the Latest Trends in Digital Security Systems
Digital Security Systems In an increasingly digitized world, the importance of robust digital security systems…